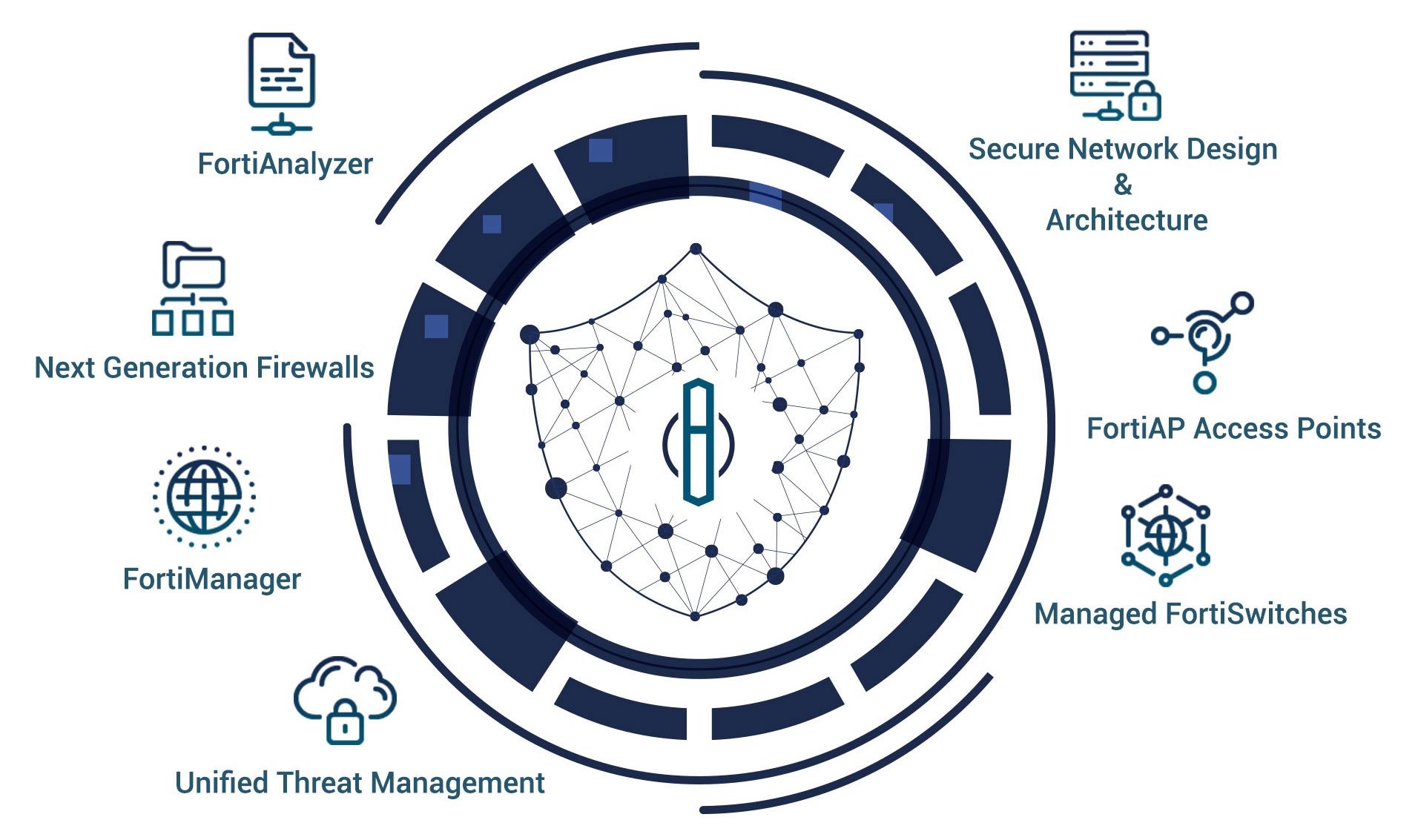
Driven by the need to move faster at a global scale while reducing costs, companies are consciously or unconsciously, undergoing digital transformation. This evolution includes the adoption of new technologies that widen the possible attack surface, leaving network perimeters vulnerable to advanced threats, resulting in a complex security environment. The Tototheo Maritime & Fortinet Security Fabric, segments the entire network — from the Internet of Things (IoT) to the cloud — to provide superior protection against sophisticated cyber threats.
Tototheo Maritime and Fortinet offer custom built vessel cyber infrastructure managed by online cloud platforms, FortiAnalyser and FortiManager, set up and managed by Tototheo Maritime with access to the customers. Tototheo Maritime now offers to the maritime industry, a complete portfolio of integrated services and solutions, when it comes to Cyber Security and Digital Transformation
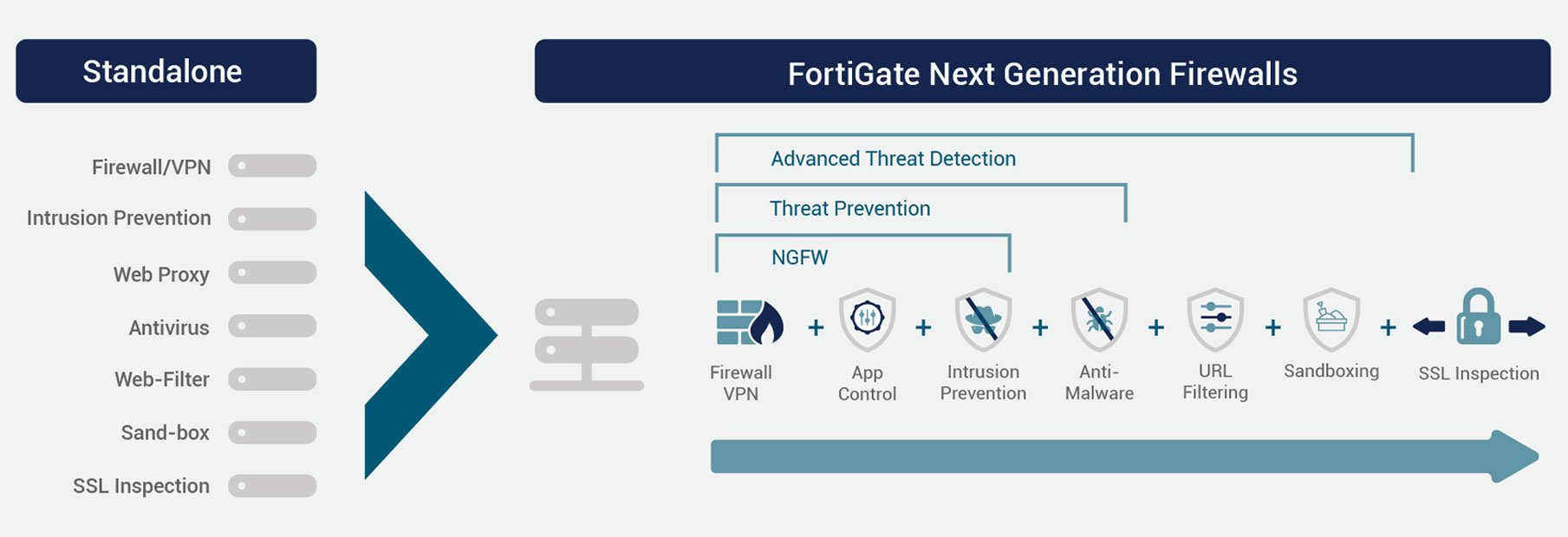
FORTIGATE:
Next Generation Firewall and Unified Threat Management
Fortigate, along with the UTM security services covers the BIMCO guidelines as well as the IMO requirements for limitation and control of network ports, protocols and services.
UTM Security Services:
 Application control: allow, deny or restrict access to applications or categories of applications
Application control: allow, deny or restrict access to applications or categories of applications
 Intrusion prevention system: detect, block and protect against latest network intrusions
Intrusion prevention system: detect, block and protect against latest network intrusions
 Antivirus: protect your systems against viruses, spyware on an application layer
Antivirus: protect your systems against viruses, spyware on an application layer
 URL Filtering: protection by blocking access to malicious, hacked or inappropriate websites
URL Filtering: protection by blocking access to malicious, hacked or inappropriate websites
 Sandboxing: execute malicious files in an isolated environment in order to analyze and report regarding a potential threat before infecting any operational systems
Sandboxing: execute malicious files in an isolated environment in order to analyze and report regarding a potential threat before infecting any operational systems
 SSL inspection: gain visibility into encrypted traffic and prevent encrypted malware reaching your network
SSL inspection: gain visibility into encrypted traffic and prevent encrypted malware reaching your network
 Prevention of unknown sophisticated threats is achieved using the above combination of technologies.
Prevention of unknown sophisticated threats is achieved using the above combination of technologies.
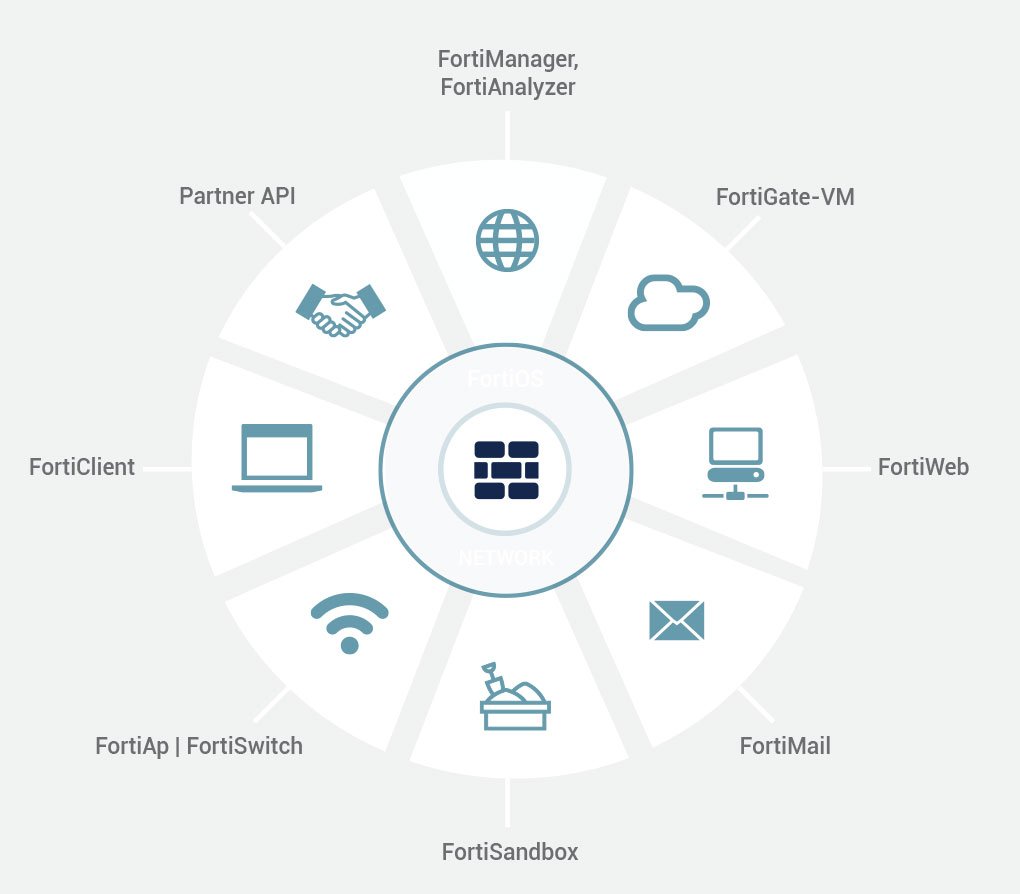
SECURITY FABRIC
Visibility, integration and automated response to threats across all Fortinet ecosystem. FortiGate NGFW with the Forti OS and Forti CPUs along with the FortiAnalyzer is the foundation of the Security Fabric, expanding security via visibility and control by tightly integrating with other Fortinet security products using the FortiLink protocol.
Features & Benefits
High-performance threat protection
Industry’s highest threat protection and SSL inspection performance to protect from malware attacks hiding in encrypted traffic
Validated security effectiveness
Independently certified and continuous threat intelligence updates provide robust protection from known and unknown attacks
Protect mission critical applications
Highly scalable segmentation and ultra-low latency to protect network segments
Continuous risk
assessment via automation
Leverage automated workflow and auditing features to deal with scarce security staff and continuously maintain compliance posture
Security Fabric
Integration
Intelligently share threats across the entire digital attack surface to provide quick and automated protection
Enterprise class
security management
Deliver consistent security policy - Single pane-of-glass to manage security assets irrespective of location and form factor
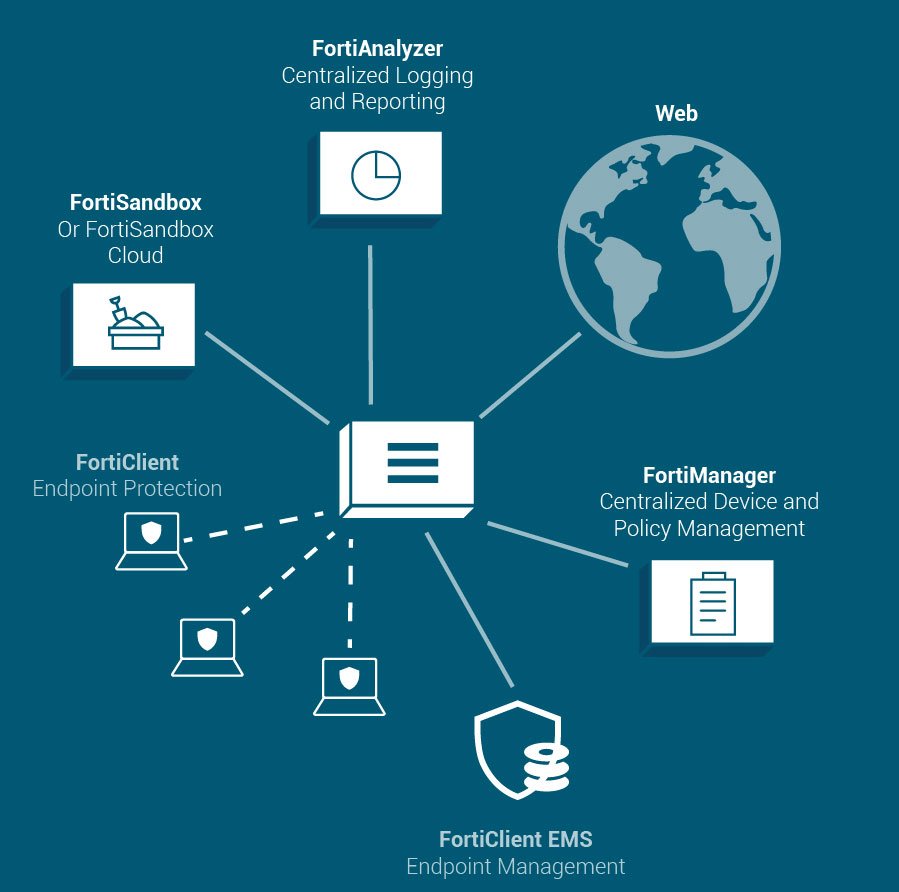
FORTICLIENT:
End Point Protection
FortiClient strengthens end point security through integrated visibility, control, and proactive defence. With the ability to discover, monitor, and assess endpoint risks, you can ensure end point compliance, mitigate risks, and reduce exposure. FortiClient proactively defends against advanced attacks.
Its tight integration with the Security Fabric enables policy-based automation to contain threats and control outbreaks.
FortiClient is compatible with Fabric-Ready partners to further strengthen enterprises’ security posture.
Features & Benefits
 Unified endpoint features including compliance, protection, and secure access into a single, modular lightweight client.
Unified endpoint features including compliance, protection, and secure access into a single, modular lightweight client.
 End-to-end threat visibility and control by natively integrating endpoint into the Security Fabric architecture.
End-to-end threat visibility and control by natively integrating endpoint into the Security Fabric architecture.
 Advanced threat protection against exploits and advanced malware, powered by FortiGuard along with FortiSandbox integration.
Advanced threat protection against exploits and advanced malware, powered by FortiGuard along with FortiSandbox integration.
 Integrated patch management and vulnerability shielding to harden all endpoints.
Integrated patch management and vulnerability shielding to harden all endpoints.
 Simplified management and policy enforcement with Enterprise Management Server (EMS) and FortiGate, respectively.
Simplified management and policy enforcement with Enterprise Management Server (EMS) and FortiGate, respectively.
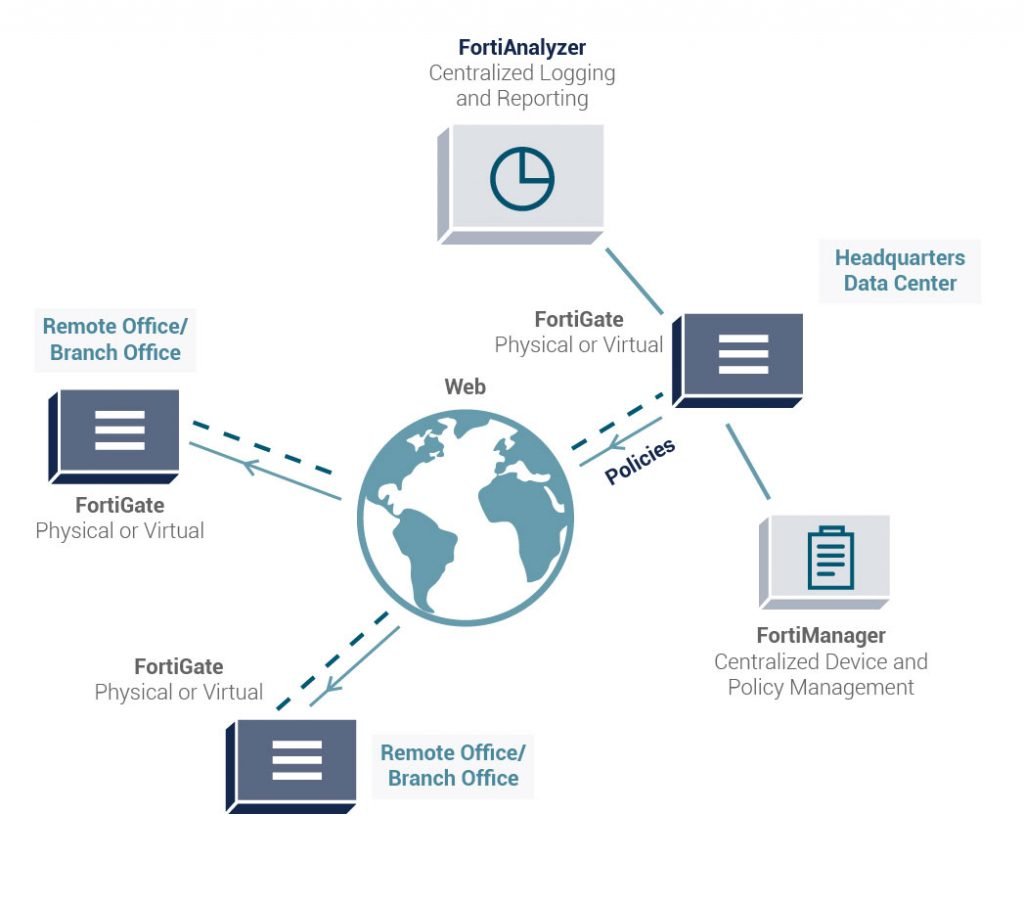
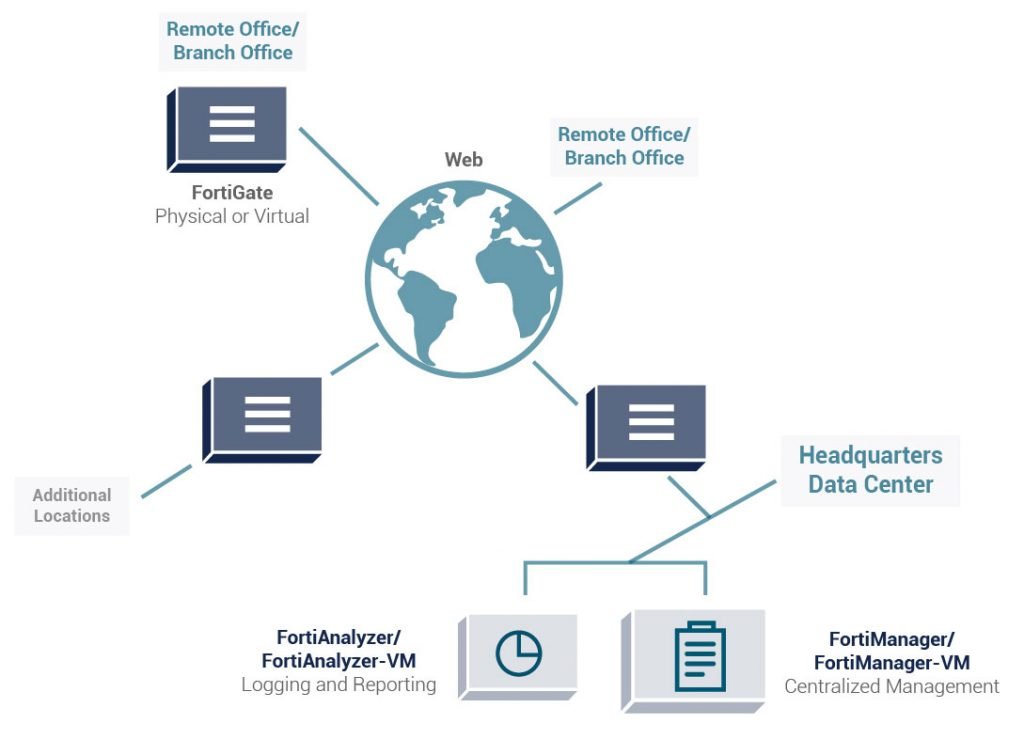
FORTIANALYZER:
NOC/SOC
An integrated security architecture with analytics-powered security and log management capabilities can address this lack of visibility. As part of the Fortinet Security Fabric, FortiAnalyzer supports analytics-powered use cases to provide better detection against breaches.
Features & Benefits
 End-to-end visibility with event correlation and threat detection
End-to-end visibility with event correlation and threat detection
Reduce time to detection by leveraging Indicator of Compromise (IOC) service to quickly identify threat across your network
 Enterprise-grade high availability
Enterprise-grade high availability
Automatically backs up the FortiAnalyzer database to up to four nodes in a cluster that can be geographically dispersed for disaster recovery. One of the secondary nodes can easily become a primary node.
 Security automation
Security automation
Reduces complexity and cost leveraging automation enabled via REST API, scripts, connectors, and automation stiches.
 Advanced compliance reporting
Advanced compliance reporting
Provides hundreds of pre-built reports and templates which are regulation-specific to make proving compliance easy.
 Multi-tenancy and administrative domains (ADOMs)
Multi-tenancy and administrative domains (ADOMs)
Separate customer data and manage domains leveraging ADOMs to be compliant and operationally effective.
FORTIMANAGER:
Remote Management System
FortiManager supports network operations use cases for centralized management, best practices compliance, and workflow automation to provide better protection against breaches.
Features & Benefits
 Centralized management:
Centralized management:
Provides a rich set of tools to centrally manage 100,000+ devices such as firewalls, switches, and access points from a single console
 Enterprise-grade high availability:
Enterprise-grade high availability:
Automatically backs up the FortiManager database to up to five nodes in a cluster that can be geographically dispersed for disaster recovery
 Security automation
Security automation
Reduces complexity and cost leveraging automation enabled via REST API, scripts, connectors, and automation stiches.
 Secure SD-WAN provisioning & monitoring:
Secure SD-WAN provisioning & monitoring:
Provision and monitor Secure SD-WAN from one console across all branch offices or campuses
 Multi-tenancy and administrative domains (ADOMs)
Multi-tenancy and administrative domains (ADOMs)
Separate customer data and manage domains leveraging ADOMs to be compliant and operationally effective.