Gap Analysis
The Gap Analysis is the starting point to every cyber security action. We audit your organisation’s infrastructure, processes, resources using a methodology focused on identifying the existence and severity of possible threats as well as the controls in place and their effectiveness. Following that we recommend the suitable countermeasures in order to limit the risks to an acceptable level.
Risk Assessment
Risk management is the range of activities undertaken by an organization to identify and understand the risks it faces. Through the Risk Assessment procedure which will be done both for the required sites (offices and vessels), the company will be in place to:
• identify the roles and responsibilities of users, key personnel, and management both ashore and on board
• identify the systems, assets, data and capabilities, which if disrupted, could pose risks to the ship’s operations and safety
• implement technical and procedural measures to protect against a cyber incident and ensure continuity of operations
• implement activities to prepare for and respond to cyber incidents
Maritime Cyber Security Plan
Tototheo Maritime offers a complete portfolio of cyber security solutions. Due to our heavy experience both in maritime and cyber security industry we have designed a unique maritime cyber security plan. We deliver tailor made Information Security Policies and Procedures that ensure your organisation is compliant with existing applicable guidelines or regulations like BIMCO, IMO, TMSA3, RightShip, NIST, ISO 27001:2013. By first analysing your needs, Tototheo will deliver a bespoke set of policies and procedures, drafted specifically to address your organisation’s requirements and needs. Our plan covers both premises and vessels requirements.
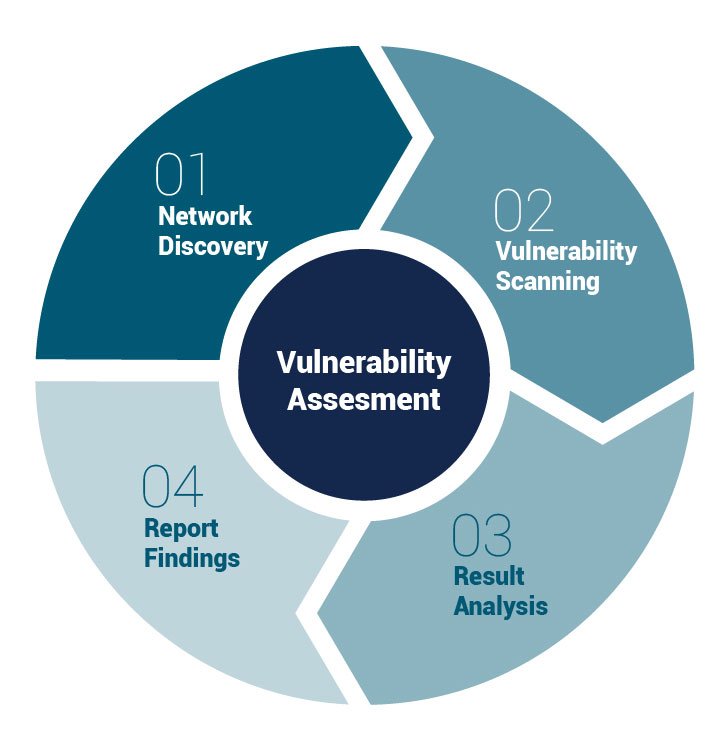
Vulnerability Assessment
The objective of a Vulnerability Assessment is to scan, investigate, analyze and report on the level of risk associated with any security vulnerabilities discovered on the public, internet facing devices and to provide your organization with appropriate mitigation strategies to address those discovered vulnerabilities.
The Risk Based Security Vulnerability Assessment methodology has been designed to comprehensively identify, classify and analyze known vulnerabilities in order to recommend the right mitigation actions to resolve the security vulnerabilities discovered.
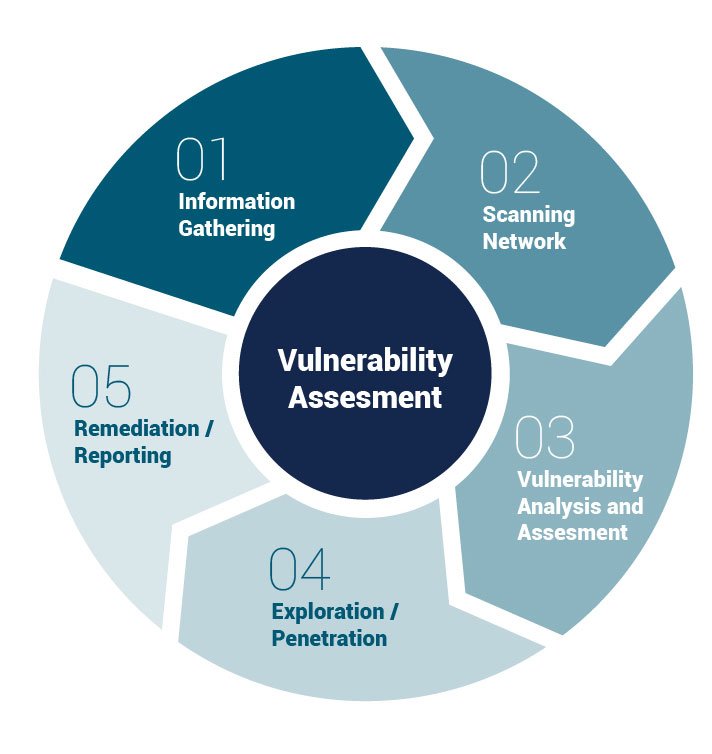
Penetration Test
The Vulnerability Assessment as well as the Penetration Test could give you a very detailed picture of what is happening to your systems. Both actions are mandatory as Vulnerability Assessment tools discover which vulnerabilities are present, but they do not differentiate between flaws that can be exploited to cause damage and those that cannot.
Penetration test attempt to exploit the vulnerabilities in a system to determine whether unauthorized access or other malicious activity is possible and identify which flaws pose a threat to the system. Penetration tests find exploitable flaws and measure the severity of each. A Penetration Test is meant to show how damaging a flaw could be in a real attack rather than find every flaw in a system. Together, penetration testing and vulnerability assessment tools provide a detailed picture of the flaws that exist in a system and the risks associated with those flaws. Tototheo uses combination of techniques in order to deliver the best possible results.